Introduction
Imagine your network is a VIP club. Firewalls act as the bouncers, only letting trusted guests in while keeping the unwanted ones out. Whether it's blocking malicious traffic or allowing secure data flows, firewalls play a crucial role in network security.
Abstract
Overview
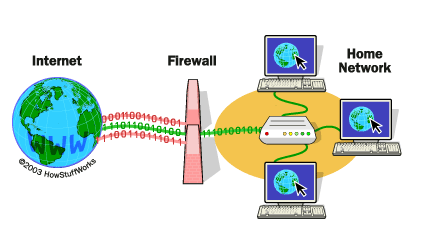
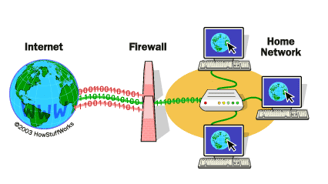
Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules. They’re essential for preventing unauthorized access and cyberattacks, whether they’re from external or internal sources. Without them, your network is vulnerable to all kinds of threats, from hackers to malware.
Firewalls are your network’s first line of defense, blocking harmful traffic while allowing legitimate communication. In this blog, we'll explore how to configure firewalls effectively to protect your network and keep cyber threats at bay.
[Disclaimer: This blog post is for informational purposes only and should not be construed as legal or financial advice. Organizations should consult with legal counsel and regulatory authorities to ensure compliance with reporting requirements.]
Mandatory
For any organization, implementing and configuring firewalls is non-negotiable. It’s a basic security measure that helps prevent external threats from breaching your internal systems, ensuring your network stays protected.
Applicability
Firewalls are applicable across all industries and company sizes. They’re particularly vital for industries handling sensitive data, such as finance, healthcare, and technology, where protecting confidential information is a top priority.
Regulatory or Company Interest?
Compliance regulations like GDPR and PCI DSS require firewalls as part of the overall security framework to protect sensitive data. A properly configured firewall helps meet these regulatory requirements.
Key Guidelines
Proper configuration – Ensure firewalls are set up to allow only necessary traffic.
Regular updates – Keep firewall software up-to-date to defend against new vulnerabilities.
Implement monitoring – Continuously monitor firewall logs to detect unusual activity.
.


Key Implications
A poorly configured firewall leaves your network exposed to cyberattacks, data breaches, and other security risks. Regular audits and testing are essential to ensure its effectiveness.
Countries with Adoption or Influence
Countries like the US, UK, and Germany have strong cybersecurity laws that emphasize the use of firewalls as part of a comprehensive network security strategy.
International Frameworks Influenced
International frameworks like NIST and ISO/IEC 27001 recommend firewalls as a critical part of network security architecture to mitigate risks.
Regional and Industry-Specific Frameworks
Industries dealing with personal and financial data, such as healthcare and banking, require strict firewall configurations to comply with regulations like HIPAA and PCI DSS.
Secure Your Digital Identity with SecureKnots
Contact us to learn more about our cybersecurity services and ensure your organization meets cybersecurity requirements.


Conclusion
Firewalls are more than just barriers; they’re the vigilant defenders of your network, keeping cyber threats at bay. Properly configured firewalls are crucial to maintaining a secure network, ensuring that harmful traffic is blocked while trusted data flows seamlessly. In today’s ever-evolving threat landscape, regular firewall audits, updates, and continuous monitoring are key to staying one step ahead.
How SecureKnots Can Help
At SecureKnots, we can help you optimize your firewall configuration and security posture with our services:
VAPT (Vulnerability Assessment & Penetration Testing): We test your firewall’s resilience against real-world attacks.
Security Awareness Trainings: Teach your team the importance of firewalls and how to avoid risky behavior that could bypass them.
Ransomware Attack Simulations: Simulate ransomware attacks to test your firewall’s ability to block malicious traffic.
Phishing Simulations: Test how well your firewall and employees defend against phishing attempts, ensuring your first line of defense is strong.
This blog focuses on the importance of securing employee access to internal systems while showcasing how SecureKnots can help organizations strengthen their access controls. It is informative and engaging, highlighting the significance of firewall Let me know if you need further adjustments!
Thank you for your attention! If you have any inquiries about cybersecurity requirements or need expert guidance, please don't hesitate to contact SecureKnots.
This should wrap up the blog and fulfill the promise made in the previous one!
Firewalls
Firewalls are the first line of defense in network security. Think of them as digital bouncers at the entrance to your network. Firewalls filter incoming and outgoing traffic, blocking harmful requests while allowing safe data through. We'll show you how to properly configure firewalls to keep unwanted visitors at bay.
WITH OUR SHORT BLOGS
STAY UP TO DATE
Copy Rights @ 2023 SecureKnots. All Rights Reserved.
CONTACT US
Contact@Secureknots.com
USA
+1-302-601-2346
+1-302-608-6708
INDIA
080-31658865
GET IN TOUCH
