NIST CSF
Components of the Framework
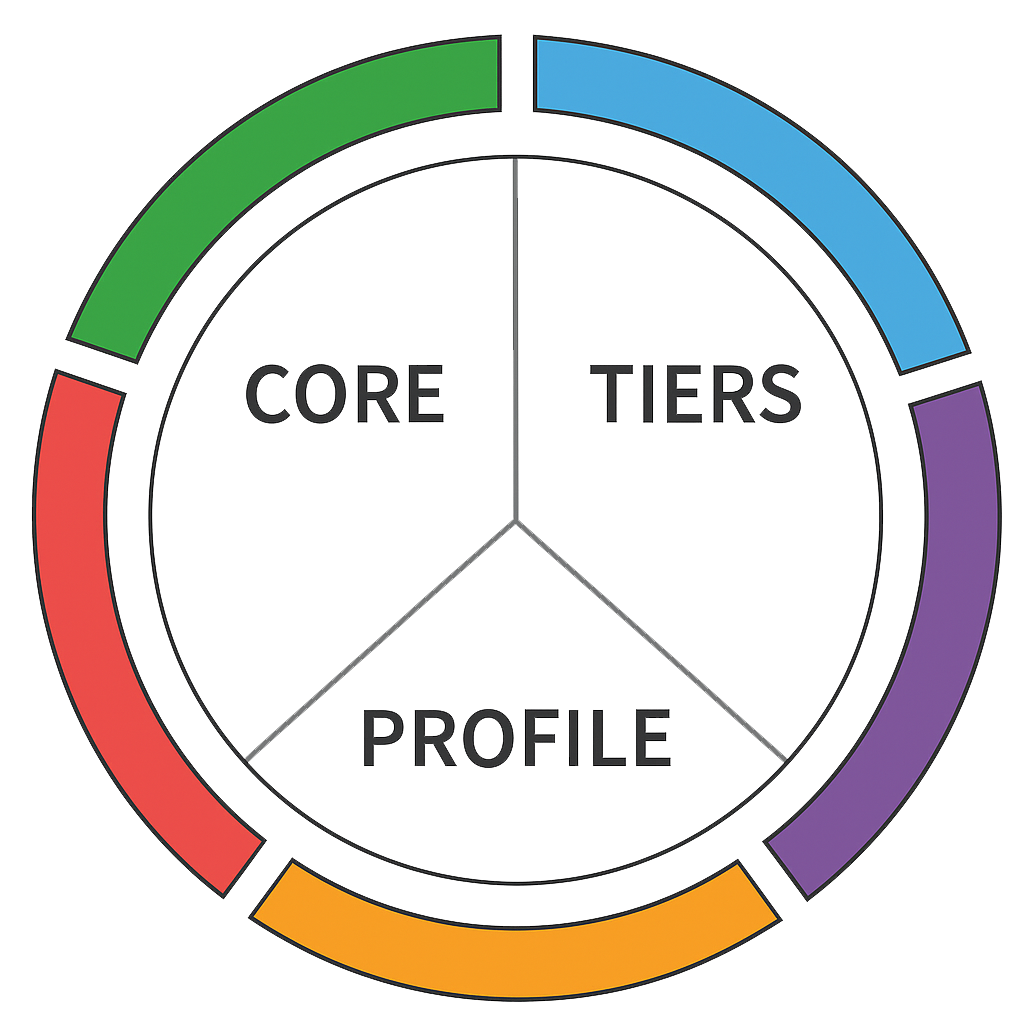
Three Primary Components
Core
Desired cybersecurity outcomes organized in a hierarchy and aligned to more detailed guidance and controls.
Profiles
Alignment of an organization’s requirements and objectives, risk appetite and resources using the desired outcomes of the Framework Core.
Implementation Tiers
A qualitative measure of organizational cybersecurity risk management practices
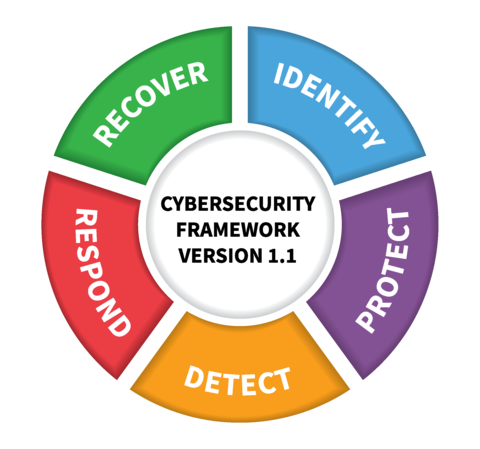
Key Framework Attributes
Principles of the Framework CORE
- Common and accessible language.
- Adaptable to many technologies, lifecycle phases, sectors and uses.
- Risk-based.
- Based on international standards.
- Living document.
- Guided by many perspectives – private sector, academia, public sector.
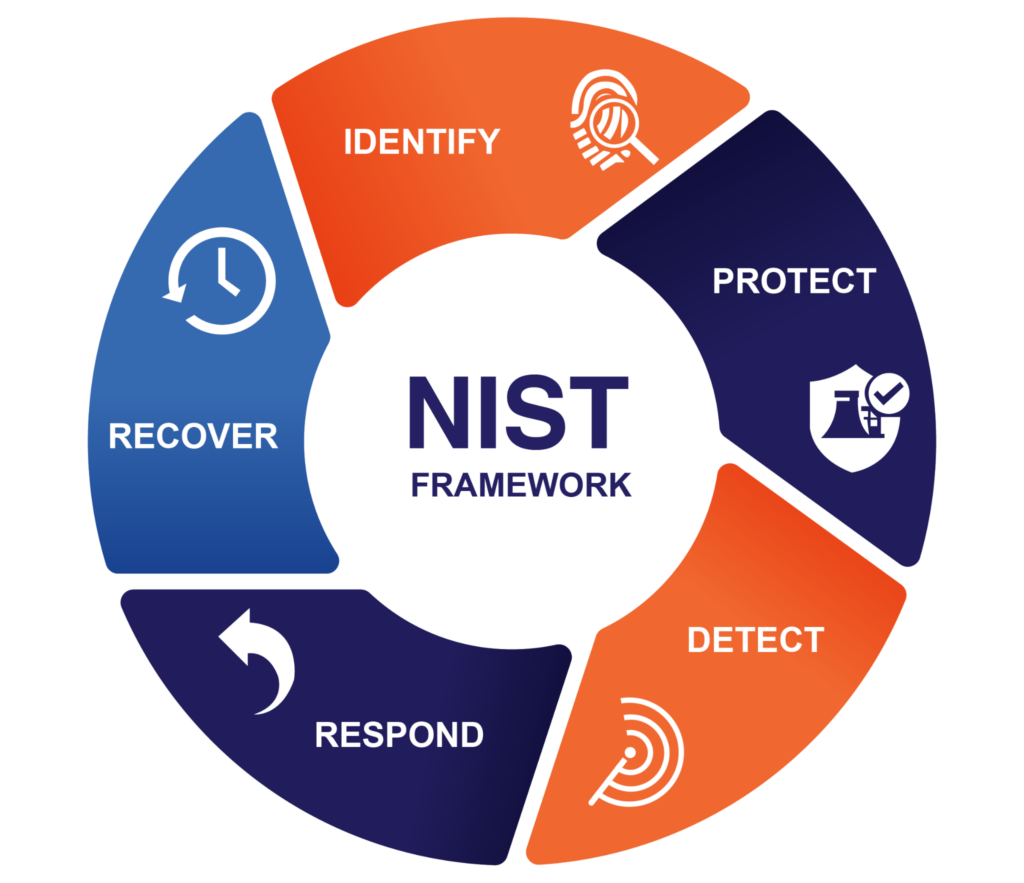
Key Benefits of NIST CSF Certification
SecureKnots offers comprehensive NIST CSF certification services tailored to help organizations implement the framework effectively. Our certified professionals conduct thorough assessments, provide expert guidance on implementing necessary security controls, and assist in remediation efforts to achieve and maintain certification.
- Regulatory Alignment: Alignment with NIST CSF framework helps organizations meet regulatory requirements and industry standards for cybersecurity, ensuring compliance with relevant regulations and guidelines.
- Continuous Improvement: NIST CSF provides a framework for continuous improvement in cybersecurity practices, enabling organizations to adapt to evolving cyber threats and challenges.
- Competitive Advantage: Achieving NIST CSF certification can give your organization a competitive edge, demonstrating your commitment to cybersecurity excellence to clients, partners, and stakeholders.
Why Choose SecureKnots for NIST Cybersecurity Framework Consulting?
Deep Understanding of NIST Framework
SecureKnots brings a profound understanding of the NIST Cybersecurity Framework, ensuring a tailored approach to meet the specific needs and challenges of your organization.
Comprehensive Framework Assessments
Our expert consultants conduct thorough assessments, providing a detailed view of your current cybersecurity posture in relation to the NIST Framework and offering actionable insights for improvement.

Collaborative Partnership
Beyond delivering reports, our consulting services foster a collaborative partnership. We engage with your team, ensuring a deep understanding of your cybersecurity processes and fostering a relationship that strengthens your overall security posture.
Your Questions, Our Expertise
Who should use the Framework?
The Cybersecurity Framework is for organizations of all sizes, sectors, and maturities.
The Framework is outcome driven and does not mandate how an organization must achieve those outcomes, it enables scalability. A small organization with a low cybersecurity budget, or a large corporation with a big budget, are each able to approach the outcome in a way that is feasible for them. It is this flexibility that allows the Framework to be used by organizations which are just getting started in establishing a cybersecurity program, while also providing value to organizations with mature programs.
How often should my organization undergo NIST CSF certification assessments to maintain certification?
What are NIST Control Families?
The NIST Cybersecurity Framework has 20 distinct control families, outlined in NIST SP 800-53, which consist of base controls and control enhancements.
Functions of the NIST Framework
The NIST CSF defines five core functions that together address cybersecurity risks. The five functions of the NIST CSF are: Identify, Protect, Detect, Respond, and Recover. These functions are further broken down into 23 Categories. NIST emphasizes that these functions must work in tandem and continuously to achieve optimal results and combat the dynamic threat landscape.
NIST also asks companies to consider their target tier of implementation or maturity. As part of that assessment, the business should consider their overall “profile,” or the unique combination of business objectives, threats, and regulatory and compliance requirements and controls that make up the company.
