Introduction
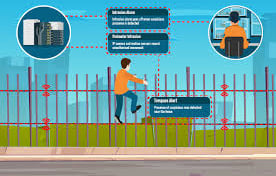
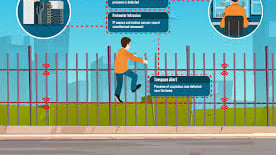
Imagine a silent guardian, constantly watching over your network. That’s what Intrusion Detection Systems (IDS) do—they monitor network traffic for suspicious activity or known attack patterns. If an attacker tries to break in, IDS can catch them early, giving you the chance to respond before damage occurs.
Abstract
Overview
IDS are security tools that track network traffic to detect potential intrusions. They analyze patterns, compare them to known attack signatures, and raise alerts if something malicious is detected. Early detection is key in preventing further damage, allowing you to contain and mitigate attacks swiftly.
Intrusion Detection Systems (IDS) are the unsung heroes of network security, alerting you to potential breaches before they escalate. In this blog, we’ll explore how IDS work, why they’re critical for cybersecurity, and how they help you stay ahead of cyber threats.
[Disclaimer: This blog post is for informational purposes only and should not be construed as legal or financial advice. Organizations should consult with legal counsel and regulatory authorities to ensure compliance with reporting requirements.]
Mandatory
Intrusion detection isn’t optional—it’s a necessary layer of defense. With cyberattacks becoming more sophisticated, having a system in place to detect and respond to threats in real-time is critical for keeping your network secure.
Applicability
IDS are applicable to all organizations, especially those handling sensitive data. Financial institutions, healthcare providers, and government agencies rely heavily on IDS to safeguard their networks against cyber intrusions.
Regulatory or Company Interest?
Regulations like GDPR, PCI DSS, and HIPAA often require monitoring for suspicious activity as part of a comprehensive security framework. IDS help companies meet these compliance requirements.
Key Guidelines
Tune IDS – Customize the system to focus on your network’s unique traffic patterns.
Monitor alerts – Respond quickly to alerts to contain potential threats.
Update signatures – Regularly update attack signatures to recognize the latest threats


Key Implications
Without IDS, intrusions might go undetected, allowing attackers to cause severe damage. Timely detection can prevent data breaches, system compromise, and financial loss.
Countries with Adoption or Influence
Countries with strong cybersecurity frameworks, like the US, UK, and Canada, have seen widespread adoption of IDS in various industries.
International Frameworks Influenced
International standards like NIST and ISO/IEC 27001 advocate for intrusion detection as part of an organization’s security protocol to ensure timely response to threats.
Regional and Industry-Specific Frameworks
Industries such as finance and healthcare, governed by standards like PCI DSS and HIPAA, require IDS to monitor and secure sensitive data and systems.
Secure Your Digital Identity with SecureKnots
Contact us to learn more about our cybersecurity services and ensure your organization meets cybersecurity requirements.


Conclusion
Intrusion Detection Systems are vital for maintaining robust cybersecurity. They help detect potential threats early, enabling rapid responses that prevent significant damage. By implementing IDS, organizations can stay one step ahead of attackers and protect their networks from breaches.
How SecureKnots Can Help
SecureKnots offers specialized services to enhance your intrusion detection capabilities:
VAPT (Vulnerability Assessment & Penetration Testing): We assess your network’s vulnerability to intrusions and identify weaknesses before attackers can exploit them.
Ransomware Attack Simulations: We simulate ransomware attacks to test your IDS's ability to detect and mitigate these threats.
Phishing Simulations: Test your network’s resilience against phishing attempts, ensuring your IDS can identify phishing-related threats.
This blog focuses on the importance of securing employee access to internal systems while showcasing how SecureKnots can help organizations strengthen their access controls. It is informative and engaging, highlighting the significance of Intrusion Detection Let me know if you need further adjustments!
Thank you for your attention! If you have any inquiries about cybersecurity requirements or need expert guidance, please don't hesitate to contact SecureKnots.
This should wrap up the blog and fulfill the promise made in the previous one!
Intrusion Detection
How do you know if someone is trying to break into your network? Intrusion detection systems (IDS) help monitor network traffic for unusual activity or known attack patterns. By detecting intrusions early, you can respond quickly and prevent further damage. We’ll explain how IDS helps you stay one step ahead of cyber threats.
WITH OUR SHORT BLOGS
STAY UP TO DATE
Copy Rights @ 2023 SecureKnots. All Rights Reserved.
CONTACT US
Contact@Secureknots.com
USA
+1-302-601-2346
+1-302-608-6708
INDIA
080-31658865
GET IN TOUCH
