Introduction
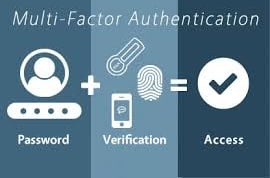
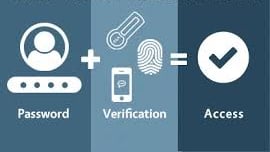
Passwords alone aren’t enough to secure your systems anymore. Imagine your password gets stolen—what happens next? Enter Multi-Factor Authentication (MFA), which adds a second line of defense to your login process. MFA combines something you know (like a password) with something you have (like a phone or token) or something you are (like a fingerprint), dramatically improving security and thwarting attackers even if they have your password.
Abstract
Overview
MFA is now a best practice for securing user accounts across industries. Whether it's for email, banking, or corporate systems, MFA prevents unauthorized access by requiring additional proof of identity. With its increasing adoption, MFA has become a game-changer in thwarting attacks like phishing and credential stuffing.
Cybersecurity is evolving, and one of the most powerful defenses against account compromise is Multi-Factor Authentication (MFA). MFA enhances security by requiring an additional form of verification beyond just passwords. In this blog, we'll explain why MFA is vital, how it works, and how businesses can implement it effectively to protect their assets. SecureKnots is here to support your MFA strategy with expert advice and services.
[Disclaimer: This blog post is for informational purposes only and should not be construed as legal or financial advice. Organizations should consult with legal counsel and regulatory authorities to ensure compliance with reporting requirements.]
Mandatory
MFA should be mandatory for accessing sensitive systems, accounts, and applications. It’s no longer a luxury—it's a must-have for any organization serious about security.
Applicability
From financial institutions to healthcare and government sectors, MFA is applicable across all industries dealing with sensitive or personal data.
Regulatory or Company Interest?
Regulations like GDPR, HIPAA, and PCI-DSS mandate strong user authentication measures, and MFA helps organizations stay compliant while enhancing security.
Key Guidelines
Implement MFA on all user accounts accessing sensitive data
Use app-based or hardware tokens for higher security
Ensure a seamless experience for users to avoid frustration


Key Implications
Implement MFA on all user accounts accessing sensitive data
Use app-based or hardware tokens for higher security
Ensure a seamless experience for users to avoid frustration
Countries with Adoption or Influence
Countries like the U.S., UK, and EU have seen widespread adoption of MFA, particularly in industries handling sensitive information.
International Frameworks Influenced
Frameworks like NIST 800-63-3 and ISO 27001 emphasize the use of MFA as a security standard for authentication processes.
Regional and Industry-Specific Frameworks
Many countries, especially in the EU and US, have enforced MFA in sectors such as finance, healthcare, and e-commerce to prevent data breaches and fraud.
Conclusion
MFA is no longer a luxury; it's a necessity. By adding a second layer of security, MFA makes it much harder for attackers to gain access, even if they know your password. It’s an essential tool in the fight against cybercrime.
Secure Your Digital Identity with SecureKnots
Contact us to learn more about our cybersecurity services and ensure your organization meets cybersecurity requirements.


How SecureKnots Can Help?
At SecureKnots, we provide comprehensive GRC consulting to help organizations implement MFA strategies tailored to their needs. Through our VAPT services, we identify weaknesses in authentication systems, while our security awareness training educates users on the importance of MFA. Additionally, our ransomware attack simulations and phishing simulations test
the effectiveness of MFA defenses in real-world scenarios, helping organizations stay ahead of emerging threats. SecureKnots ensures your MFA solution is both robust and easy to use.
This blog focuses on the importance of securing employee access to internal systems while showcasing how SecureKnots can help organizations strengthen their access controls. It is informative and engaging, highlighting the significance of strong authentication practices. Let me know if you need further adjustments!
Thank you for your attention! If you have any inquiries about cybersecurity requirements or need expert guidance, please don't hesitate to contact SecureKnots.
This should wrap up the blog and fulfill the promise made in the previous one!
Multi-Factor Authentication (MFA)
What if your password gets stolen? That’s where multi-factor authentication (MFA) comes into play. By requiring a second form of verification (like a text code or biometric scan), MFA adds an extra layer of protection. We'll explain how this simple yet effective tool can keep attackers out, even if they know your password.
WITH OUR SHORT BLOGS
STAY UP TO DATE
Copy Rights @ 2023 SecureKnots. All Rights Reserved.
CONTACT US
Contact@Secureknots.com
USA
+1-302-601-2346
+1-302-608-6708
INDIA
080-31658865
GET IN TOUCH
