Introduction
In the world of cybersecurity, securing access to critical resources is paramount. One way to achieve this is through RBAC, a system where access is granted based on roles rather than individuals. As businesses grow and evolve, managing these roles efficiently becomes a complex task. Enter Generative AI, which helps automate and streamline the process, ensuring no one has more access than they need.
Abstract
Overview
RBAC is a model designed to improve security by restricting access based on roles. Users are assigned to roles that have predefined access permissions, and as users move through an organization, their roles (and therefore their access) can be updated automatically. This ensures that permissions are always aligned with job responsibilities and organizational needs.
In the ever-evolving landscape of cybersecurity, organizations face the challenge of securing sensitive data and systems. One of the best ways to manage and mitigate risks is through Role-Based Access Control (RBAC). This approach ensures that only the right people have access to the right resources. With the rise of Generative AI, RBAC is becoming even more dynamic and automated, making it easier to maintain secure access controls.

[Disclaimer: This blog post is for informational purposes only and should not be construed as legal or financial advice. Organizations should consult with legal counsel and regulatory authorities to ensure compliance with reporting requirements.]
Mandatory
For cybersecurity professionals, implementing RBAC is not just a best practice—it's a necessity. It’s crucial for compliance with various regulations and frameworks, as well as for reducing the risk of unauthorized access and data breaches.
Applicability
RBAC applies across a range of industries, from healthcare to finance, where sensitive data needs to be protected and access needs to be tightly controlled. The flexibility and scalability of RBAC make it a key solution for organizations of all sizes.
Regulatory or Company Interest?
Organizations are increasingly adopting RBAC due to regulatory requirements like GDPR, HIPAA, and PCI-DSS, which demand strict access controls. Companies also benefit from RBAC's ability to improve operational efficiency while reducing security risks.
Key Guidelines
Clearly define roles within your organization.
Assign permissions based on the principle of least privilege.
Regularly review roles and permissions to ensure they align with current job functions.
Use automation where possible to reduce human error.
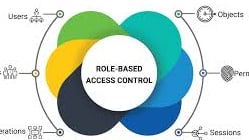
Key Implications
By adopting RBAC, organizations can better manage who has access to what. This reduces the risk of insider threats and unauthorized access, streamlining the process of auditing and compliance.
Countries with Adoption or Influence
Countries like the U.S., EU nations, and Canada have adopted stringent cybersecurity frameworks and regulations that align with RBAC principles. Many organizations worldwide are implementing RBAC as part of their broader cybersecurity strategy.
International Frameworks Influenced
RBAC is embedded in several international cybersecurity frameworks such as ISO 27001, NIST, and CIS Controls, which guide organizations in setting up robust access control mechanisms.
Regional and Industry-Specific Frameworks
In sectors like healthcare (HIPAA), finance (PCI-DSS), and government, RBAC is a critical element of compliance frameworks, ensuring that only authorized personnel access sensitive information.
Secure Your Digital Identity with SecureKnots
Contact us to learn more about our cybersecurity services and ensure your organization meets cybersecurity requirements.
Conclusion
RBAC remains a cornerstone of modern cybersecurity strategies, ensuring that organizations maintain control over their sensitive resources. As technological advancements like Generative AI continue to influence cybersecurity practices, RBAC is set to become more efficient, automated, and secure.
How SecureKnots Can Help?
At SecureKnots, we specialize in GRC consulting and security audits, helping organizations implement and maintain RBAC systems effectively. Our internal and external audit services, alongside VAPT and phishing simulations, ensure that your access controls are functioning as intended. Additionally, our security awareness training can help employees understand the importance of access management, making RBAC part of the organization’s security culture. Let SecureKnots guide you in securing your organization with the best access control practices.
This blog focuses on the importance of securing employee access to internal systems while showcasing how SecureKnots can help organizations strengthen their access controls. It is informative and engaging, highlighting the significance of Role-Based Access Control (RBAC). Let me know if you need further adjustments!
Thank you for your attention! If you have any inquiries about cybersecurity requirements or need expert guidance, please don't hesitate to contact SecureKnots.
This should wrap up the blog and fulfill the promise made in the previous one!
Role-Based Access Control (RBAC)- Keeping It Organized
Think of Role-Based Access Control (RBAC) as an organized filing system. Instead of handing out access to everything, you categorize users into different groups (or roles). Each role gets access to specific resources. Generative AI can take it a step further by automatically updating roles as users move through an organization, ensuring no one has more access than they should. We’ll explore this concept in depth in future posts.
WITH OUR SHORT BLOGS
STAY UP TO DATE
Copy Rights @ 2023 SecureKnots. All Rights Reserved.
CONTACT US
Contact@Secureknots.com
USA
+1-302-601-2346
+1-302-608-6708
INDIA
080-31658865
GET IN TOUCH
