Introduction
Think of network segregation like a well-organized office building with secure rooms and open spaces. By creating separate “zones,” you can ensure that sensitive systems are protected from general access. This tactic reduces the risk of hackers spreading throughout your infrastructure, making your network far less vulnerable.
Abstract
Overview
Network segregation involves dividing your network into different zones, each with its own security policies and access controls. By isolating critical systems, like databases or servers, from less sensitive areas, you can contain potential breaches and prevent attackers from moving laterally across your entire network.
Network segregation is a key strategy for enhancing security. By dividing your network into distinct sections with varying access levels, you can limit the damage caused by a breach. In this blog, we explore how to effectively segregate networks to minimize risk and improve security.


[Disclaimer: This blog post is for informational purposes only and should not be construed as legal or financial advice. Organizations should consult with legal counsel and regulatory authorities to ensure compliance with reporting requirements.]
Mandatory
Network segregation is essential for maintaining strong security. It’s not just a best practice—it's a critical measure to limit the damage in case of a breach. Without proper segregation, hackers can easily access and move across your network, making it harder to contain an attack.
Applicability
Segregation applies to all industries, particularly those handling sensitive data like finance, healthcare, and government. The more critical the systems, the more important it is to implement network zones with restricted access.
Regulatory or Company Interest?
Compliance frameworks like PCI DSS and HIPAA emphasize network segmentation to protect sensitive data. Segregating networks also helps fulfill organizational security policies.
Key Guidelines
Create security zones – Isolate sensitive systems from general access.
Control access – Use firewalls and VLANs to enforce strict access controls.
Monitor and audit – Regularly monitor traffic between zones to detect potential threats.


Key Implications
Without proper network segregation, a breach could quickly compromise your entire network. A well-segregated network limits the impact of cyberattacks, making it easier to respond and recover.
Countries with Adoption or Influence
Countries like the US, EU member states, and Japan have strong cybersecurity regulations encouraging network segmentation to protect critical infrastructure.
International Frameworks Influenced
International standards like NIST and ISO/IEC 27001 support the concept of network segmentation to improve security by isolating vulnerable areas.
Regional and Industry-Specific Frameworks
Industries such as banking and healthcare often require network segregation to meet security and regulatory requirements, including PCI DSS and HIPAA compliance.
Secure Your Digital Identity with SecureKnots
Contact us to learn more about our cybersecurity services and ensure your organization meets cybersecurity requirements.
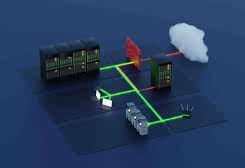

Conclusion
Segregating networks is a powerful way to enhance your organization's security posture. By creating secure zones and enforcing access control, you limit the risk of cyberattacks spreading across your infrastructure. A well-organized network is a safe network, and with the right measures in place, you can significantly reduce your exposure to threats.
How SecureKnots Can Help
At SecureKnots, we offer comprehensive services to support network segregation and overall security:
VAPT (Vulnerability Assessment & Penetration Testing): We test your network for weaknesses in segmentation, helping you identify and fix potential vulnerabilities.
Security Awareness Trainings: Equip your team with the knowledge of how to maintain secure access and avoid compromising sensitive zones.
Ransomware Attack Simulations: Simulate attacks to assess how well your network segregation holds up against ransomware threats.
Phishing Simulations: Test the effectiveness of your network’s defenses against phishing, a common vector for lateral movement within unsegregated networks.
This blog focuses on the importance of securing employee access to internal systems while showcasing how SecureKnots can help organizations strengthen their access controls. It is informative and engaging, highlighting the significance of Segregate Networks Let me know if you need further adjustments!
Thank you for your attention! If you have any inquiries about cybersecurity requirements or need expert guidance, please don't hesitate to contact SecureKnots.
This should wrap up the blog and fulfill the promise made in the previous one!
Segregate Networks
A well-organized network is a secure network. Segregating networks means creating different sections (or "zones") in your network, each with different levels of access. By separating critical systems from general user access, you reduce the risk of a hacker spreading throughout your entire infrastructure.
WITH OUR SHORT BLOGS
STAY UP TO DATE
Copy Rights @ 2023 SecureKnots. All Rights Reserved.
CONTACT US
Contact@Secureknots.com
USA
+1-302-601-2346
+1-302-608-6708
INDIA
080-31658865
GET IN TOUCH
