Introduction
Just like a company has different departments (finance, marketing, customer service), digital systems have different user roles, each with specific responsibilities and access levels. Properly managing these roles ensures that users only have access to the data and tools they need to perform their jobs—and nothing more. This is crucial in maintaining security and efficiency.
Abstract
Overview
User roles are at the heart of security. When assigning roles, you must ensure that permissions are carefully controlled to limit access based on a user’s role in the organization. By automating role assignments with AI, businesses can ensure that only the right people have access to sensitive data, improving both security and operational efficiency.
In the digital world, user roles define what people can and cannot do—just like in a company where different departments have different responsibilities. But how do we ensure users only have access to what they need, no more, no less? This is where AI steps in to automatically assign roles based on necessity. Let’s dive into how effective role management keeps your digital systems secure and compliant.
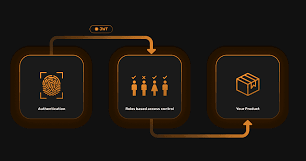
[Disclaimer: This blog post is for informational purposes only and should not be construed as legal or financial advice. Organizations should consult with legal counsel and regulatory authorities to ensure compliance with reporting requirements.]
Mandatory
Role management is mandatory for any organization looking to secure digital systems and comply with regulations. Without a clear structure of roles, you risk exposing sensitive data or granting unnecessary access.
Applicability
This is applicable to any organization handling sensitive data—whether you're in healthcare, finance, or tech, user roles are essential for protecting your systems.
Regulatory or Company Interest?
Regulations such as GDPR, HIPAA, and PCI-DSS require strict controls over who has access to sensitive data, making proper role-based access management a regulatory necessity.
Key Guidelines
Implement role-based access control (RBAC)
Regularly review and update roles to adapt to changing job functions
Automate role assignment with AI to ensure accuracy and efficiency

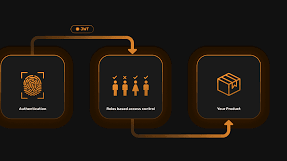
Key Implications
Clear role management reduces the risk of insider threats, ensures compliance, and improves operational efficiency. Inadequate role management can lead to unauthorized access, data breaches, and compliance violations.
Countries with Adoption or Influence
Countries with strict data protection laws like the EU, US, and Canada have adopted role-based access control as part of their national cybersecurity frameworks.
International Frameworks Influenced
Standards like NIST 800-53 and ISO 27001 emphasize the importance of role-based access control in securing sensitive information.
Regional and Industry-Specific Frameworks
In healthcare and finance, industries have even stricter role management requirements to ensure that only authorized individuals can access confidential data.
Conclusion
User roles and access controls are foundational elements of a secure digital environment. By adopting AI-powered solutions to streamline role assignments and access management, organizations can minimize the risk of data breaches and ensure compliance with industry standards.
Secure Your Digital Identity with SecureKnots
Contact us to learn more about our cybersecurity services and ensure your organization meets cybersecurity requirements.


How SecureKnots Can Help?
SecureKnots assists in implementing role-based access control (RBAC) through our GRC consulting and security audits. Our VAPT services identify potential vulnerabilities in your access controls, while security awareness training educates employees about the importance of role-specific access. Additionally, we offer ransomware and phishing simulations to test the effectiveness of your role management system in real-world scenarios. With SecureKnots, your role-based access strategy is both secure and efficient.
This blog focuses on the importance of securing employee access to internal systems while showcasing how SecureKnots can help organizations strengthen their access controls. It is informative and engaging, highlighting the significance of User Roles. Let me know if you need further adjustments!
Thank you for your attention! If you have any inquiries about cybersecurity requirements or need expert guidance, please don't hesitate to contact SecureKnots.
This should wrap up the blog and fulfill the promise made in the previous one!
User Roles- What Are You Allowed to Do?
Just like at a company, not everyone has the same responsibilities—some people are in charge of the budget, some handle marketing, and others deal with customer service. The same idea applies to your digital systems. Different user roles come with different levels of access and permissions. In our detailed posts, we’ll break down how AI can automatically assign the right roles to the right people and make sure each user gets exactly what they need to do their job—and nothing more.
WITH OUR SHORT BLOGS
STAY UP TO DATE
Copy Rights @ 2023 SecureKnots. All Rights Reserved.
CONTACT US
Contact@Secureknots.com
USA
+1-302-601-2346
+1-302-608-6708
INDIA
080-31658865
GET IN TOUCH
